Intel Trusted Execution Technology, open-source now!

Finally after six month of development and testing we can release our last part of the Intel TXT support that we did for a customer. Now where we have everything open-source and documented it will lead to better understanding and integration for Intel platform security features. The publicly disclosed and updated Intel document can be found here. More information about the technology itself are available through the Intel homepage.
Our Intel TXT implementation doesn't contain Converged BootGuard and Intel Trusted Execution Technologies support (CBnT) yet, which was introduced with Cannon/Coffee/Whiskey/Ice Lake platforms.
How does it work?
Intel TXT is a technology which was developed to support two major features.
- BIOS Initial Boot Block (IBB) code protection which ensures that the initial code from the reset vector is hashed and stored in the TPM Platform Configuration Register.
- Measured Launch Environment uses "Security by Isolation" (similar to Intel SGX) to protect code with local attestation and isolation mechanisms like IOMMU. It is also a Dynamic Root of Trust for Measurement (DRTM) technology.
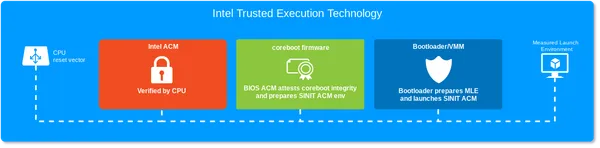
Intel Trusted Execution Technology feature overview
Both features require different Authenticated Code Modules (SINIT and BIOS ACM) which are signed blobs from Intel. The ACM is loaded into the CPU cache and gets verified before execution. ACM's are used as Dynamic Root of Trust because they can anytime securely launched during runtime. Additionally to the signed blobs it requires a securely provisioned Trusted Platform Module as Static Root of Trust.
How does it integrate with coreboot?
We have splited the integration into four parts:
- Intel Firmware Interface Table (FIT) Linux userspace tooling
- Integration of IBB measurements of Google Verified Boot
- Measured Launch Environment ramstage driver
- Memory scrubbing API and x86 PAE support
The Intel FIT is an interface for easy firmware intercommunication. We have implemented a Linux userspace tool which packs the Intel TXT related parts (FIT header, blobs, coreboot firmware) into one single binary. It is quite useful because it is required to implement other Intel security technologies, e.g. Intel BootGuard or CBnT. The new tool is now part of the coreboot build process and can be used in conjunction with Google Verified Boot (vboot).
The most challeging part was MLE ramstage driver with 2000 lines of code (C, Assembly). This driver makes it possible to set up a Measured Launch Environment from Bootloader/OS side. The MLE feature is the most well known and often used with the tboot hypervisor. There is also a new project called Trenchboot which is worth to checkout!
Another important feature is the memory scrubbing. It has to be done if secrets are still left in system memory after an abnormal MLE teardown. Therefore we had to implement x86 Physical Address Extension to speed up the scrubbing process up to ~1.5s for 16GB of memory. On newer platforms the ACM's can wipe the system memory instead of the trusted BIOS firmware.
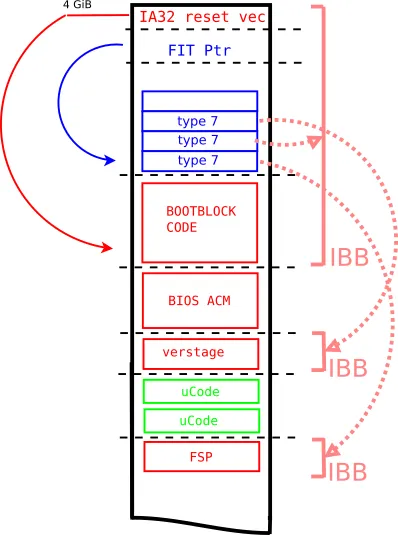
Measures the red firmware parts and extents it into the TPM PCR-0
We have tested Intel TXT on the OCP Wedge100s and Facebook Watson platform. If you ask why you can't find them in the coreboot source tree, they got lately removed because the coreboot project deprecated the romcc technology stack for older platforms. More details about the coreboot integration are available via coreboot documentation.
If you want to know more about our firmware and security work please feel free to contact us at cybersecurity@9elements.com